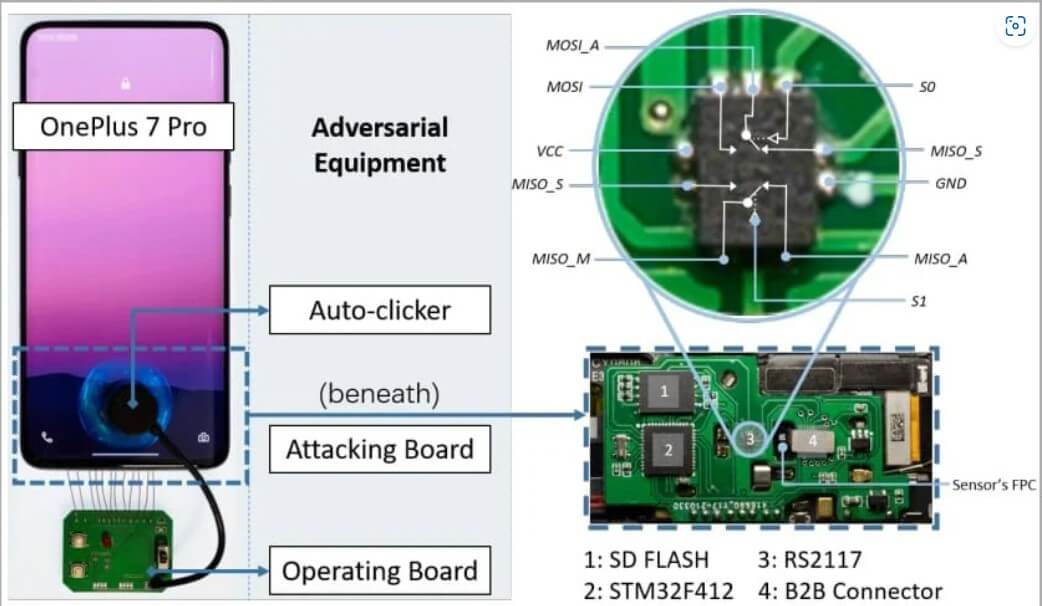
A recent breakthrough in smartphone security research by Chinese experts has revealed a novel form of attack specifically aimed at mobile devices. Known as BrutePrint, this type of brute-force attack effectively circumvents fingerprint authentication measures. The researchers successfully bypassed the security features put in place to counter brute-force attacks, including attempt limits and liveness detection, thereby compromising the effectiveness of these safeguards.
Brute-force attacks involve multiple trial-and-error attempts to crack a password or key, aiming to gain unauthorized access to accounts.
A team of experts conducted tests on ten different smartphone models to assess this new method. The results revealed that all Android and HarmonyOS (Huawei) phones were vulnerable to unlimited login attempts, while iOS devices allowed for an additional ten attempts.
Understanding BrutePrint Attack Mechanism
A group of researchers from Tencent Labs and Zhejiang University have provided insights into the inner workings of BrutePrint attacks. They successfully exploited two vulnerabilities known as Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL). Additionally, they discovered that the Serial Peripheral Interface (SPI) used in the fingerprint sensors’ biometric data lacked adequate safeguards, leaving it vulnerable to potential man-in-the-middle (MITM) attacks capable of stealing fingerprint images.
The primary objective of a fingerprint brute-force attack is to enable unauthorized individuals to make an unlimited number of attempts to unlock a device using various fingerprint combinations.
To conduct a BrutePrint attack, hackers require physical proximity to the targeted device, access to a fingerprint database, and approximately $15 worth of equipment.
A vulnerability known as Cancel-After-Match-Fail (CAMF) introduces a deliberate error into the fingerprint data during the authentication process, effectively halting the authentication. Exploiting this vulnerability, threat actors gain the ability to attempt an unlimited number of fingerprints on the Android device without triggering the security system.
In addition, the Match-After-Lock (MAL) bug allows attackers to persist with authentication attempts even when the device is in “lockout mode.” Normally, lockout mode is activated after a certain number of failed attempts and is designed to prevent further authentication for a period of time.
To summarize, the BrutePrint attack employs a technique that manipulates the transfer system, causing all the images from the fingerprint database to appear as if they were scanned by the targeted device. This deceptive tactic tricks the scanning sensor into perceiving the manipulated images as valid, bypassing the security measures in place.
Findings from the BrutePrint Tests
The BrutePrint tests involved examining the attack method on both Android and iOS devices. The outcomes of the tests revealed that vulnerabilities were present in all devices, rendering them susceptible to exploitation.
In the case of Android devices, the flaw lies in the fact that they allow an unlimited number of attempts to authenticate using fingerprints, thereby making it possible for an attacker to employ brute-force tactics to unlock the device. Conversely, iOS devices demonstrated a significantly stronger authentication security system that effectively combats brute-force attacks.